Security is actually a hot topic and it has been for quite a while as well. Many years ago, viruses were the only concerns of system administrators actually. Viruses were really common that it led the way for an amazing range of virus prevention tools. Nowadays, barely anyone would think of running an unprotected computer actually. In this article, we are going to talk about Free Intrusion Detection Software For Windows. Let’s begin!
Safeguarding the security of your IT infrastructure is not an easy task. There are so many components in order to protect, and no firewall is entirely foolproof actually. Cyberattacks are constantly evolving, along with the express intention of breaching your defenses and compromising your systems, and more come to light each and every day. Keeping pace along with these developments need your security solution to be adaptable and comprehensive.
Well, an intrusion detection system (IDS) is actually a vital element of a truly successful solution. It actually flags up inbound and outbound malicious traffic so that you can take proactive steps to safeguard your network too. An effective IDS basically keeps your IT personnel informed, so they can respond and with precision to a potential threat as well.
Contents
- 1 Intrusion Detection System (IDS)
- 2 Types of Intrusion Detection
- 3 Network-Based Intrusion Detection System (NIDS)
- 4 Host-Based Intrusion Detection System (HIDS)
- 5 NIDS vs. HIDS
- 6 The Best Free Intrusion Detection Tools
- 7 OSSEC
- 8 Snort | intrusion detection software for windows
- 9 Suricata | intrusion detection software for windows
- 10 Open Wips-NG | intrusion detection software for windows
- 11 Security Onion | intrusion detection software for windows
- 12 Sagan | intrusion detection software for windows
- 13 Conclusion
Intrusion Detection System (IDS)
It is a security software that actually monitors the network environment for suspicious or unusual activity. And then it alerts the administrator if something comes up.
The importance of an Intrusion Detection System cannot really emphasize enough. IT departments in organizations deploy the system in order to get insights into potentially malicious activities. That basically happens within their technological environments.
Plus, it allows information to transfer between departments and organizations in an increasingly safe and also trustworthy way. In many ways, it is an upgrade on other cybersecurity technologies like Firewalls, Antivirus, Message encryption, as well.
Well, firewalls and anti-malware programs are just one small part of a comprehensive approach to security as well. When a network grows, and also unknown or new devices regularly jump in and out, then you need intrusion detection software. This software should capture snapshots of your entire system, via knowledge of potential intrusions to proactively avoid them. Intrusion detection system software is mostly combined with components designed in order to protect information systems as part of a wider security solution.
Types of Intrusion Detection
An intrusion detection system basically comes have two types: a host-based intrusion detection system (HIDS) or a network-based intrusion detection system (NIDS). To put it simply, a HIDS system basically examines the events on a computer that is connected to your network. Rather than examining traffic passing through the system. just like its name suggests, it’s based around the host. A NIDS, on the other hand, examines the network traffic actually.
Network-Based Intrusion Detection System (NIDS)
A system that examines and also analyzes network traffic. A network-based intrusion detection system must feature a packet sniffer, that gathers network traffic, as standard actually. However, NIDSs can vary, they typically include a rule-based analysis engine, that can be customized with your own rules. In most of the cases, NIDS has a user community producing rules you can also import directly, to save you time. It may take some time to get familiar along with the rule syntax of your chosen NIDS. And being able to import from the user community can actually make the initial NIDS implementation feel like less of a steep learning curve as well.
Well, NIDS rules also facilitate selective data capture. This is important as if you were to feed all your traffic into files or run it through a dashboard. Then data analysis would be really much impossible. So, if you guys have a rule designed in order to flag up suspicious HTTP traffic. Then your NIDS will filter out irrelevant data and only save HTTP packets with particular characteristics as well. This basically keeps the system from being overwhelmed.
A NIDS program mostly gets installed on a specific piece of equipment. The high-end, enterprise-grade solutions that typically come in the form of a network kit along with the program built-in. A NIDS needs a sensor module for picking up traffic, however, you do not necessarily need to pay out for expensive hardware. You could load a sensor module onto a LAN analyzer or specify a device in order to run the task. Just make sure the device that you choose has enough clock speed; otherwise, it will actually cause your network to lag.
Host-Based Intrusion Detection System (HIDS)
Rather than examining the traffic, host-based intrusion detection systems because examine the events on a computer. That is connected to your network, through looking into admin file data. This mostly includes configuration and log files as well. A HIDS will then back up your configuration files so that you can restore previous settings. If a virus affects system security through altering the device setup. A HIDS can’t really block these alterations, however, it should notify you so you can act to rectify or avoid them.
Hosts monitored by HIDSs must have the software installed actually. Your HIDS can also monitor just one device if you’d like, however, it’s common to install a HIDS on every piece of equipment that is connected to your network. This avoids any configuration changes on devices from being overlooked actually. But, if you have a HIDS on each device, logging in to each one individually in order to access data is time-consuming and labor-intensive.
That’s why you guys will need a distributed HIDS system with a centralized console or control module as well. So that you can view the feedback for every host from one location. It is necessary for the system you select to encrypt the information passing between the hosts and the centralized console.
NIDS vs. HIDS
So, should you choose for a NIDS or a HIDS? The short answer: you should probably have both actually. A NIDS provides you far more monitoring capacity than a HIDS can actually, that allows you to intercept cyberattacks in real-time as well. A HIDS, on the other hand, is only able to identify if something is wrong when a setting or file has already been altered. Through combining these two systems, you can achieve a preventive and also responsive solution as well. Having a HIDS is necessary as HIDS activity is less aggressive than NIDS activity—for a start. A HIDS should not use as much CPU actually. Neither type of system generates network traffic as well.
The Best Free Intrusion Detection Tools
Well, intrusion detection systems can be expensive, really expensive. However, there are quite a few free alternatives available out there. Let’s have a look at the best of them.
OSSEC
OSSEC, that stands for Open Source Security, is by far the leading open-source host intrusion detection system actually. It is basically owned by Trend Micro, one of the leading names in IT security. The software, when installed on Unix-like operating systems, basically focuses on log and configuration files. It also creates checksums of essential files and periodically validates them. That alert you if something odd happens. On the Windows, the system also keeps an eye for unauthorized registry modifications as well.
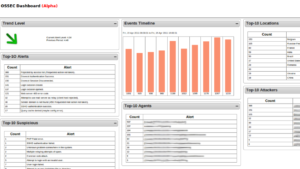
The IDS software can also monitor unauthorized registry modifications on Windows and any attempts on Mac-OS in order to get to the root account. If you want to make Intrusion Detection management easier, then OSSEC consolidates information from all the network computers in a single console. An alert is displayed on this console whenever the IDS detects something actually.
Snort | intrusion detection software for windows
Well, just like OSSEC was the top open-source HIDS, Snort is the leading open-source NIDS. Snort is basically more than an intrusion detection tool. It’s also a packet sniffer and a packet logger as well.
The leading NIDS tool, Snort is actually free to use. And it is also one of the few Intrusion Detection Systems that can be installed on Windows. Snort is not only an intrusion detector, however, it is also a Packet logger and also a Packet sniffer. But, the most necessary feature of this tool is intrusion detection actually.
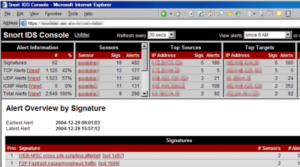
Like Firewall, Snort also has a rules-based configuration. You can download the base rules from the snort site and then customize it according to your requirements. Snort performs intrusion detection via both Anomaly-based and Signature-based methods as well.
Plus, the basic rules of Snort, we can use it in order to detect a huge variety of events. That includes OS fingerprinting, SMB probes, CGI attacks, Buffer overflow attacks, and also Stealth port scans as well.
Suricata | intrusion detection software for windows
Suricata advertises itself as an intrusion detection and also prevention system and as a complete network security monitoring ecosystem as well. One of these tool’s best benefit over Snort is that it works all the way up to the application layer also.
A robust network threat detection engine, Suricata is actually one of the main alternatives to Snort. But, what makes this tool better than snort is that it performs data collection at the application layer as well. Plus, this IDS can perform intrusion detection, network security monitoring, and also inline intrusion prevention in real-time.
The Suricata tool also understands higher-level protocols. Like SMB, FTP, and HTTP and can also monitor lower-level protocols such as UDP, TLS, TCP, and ICMP. Lastly, this IDS gives network administrators along with file extraction capability to allow them in order to inspect suspicious files on their own.
Open Wips-NG | intrusion detection software for windows
Well, an IDS meant specifically for wireless networks. The Open WIPS-NG in an open-source tool comprising of three main components i.e. sensor, server, and interface component as well. Every WIPS-NG installation can include only one sensor and this is a packet sniffer that can maneuver wireless transmissions in mid-flow as well.
The intrusion patterns are basically detected by the server program suite that contains the engine for analysis as well. The system’s interface module is a dashboard showcasing alerts and also events to the administrator of the system actually.
Well, not everyone likes Open WIPS NG, though. The product is from the same developer as Aircrack NG a wireless packet sniffer and also a password cracker that is part of every WiFi hacker’s toolkit as well. However, on the other hand, given his background, we can also assume that the developer knows really a bit about Wi-Fi security.
Security Onion | intrusion detection software for windows
Security Onion is an interesting beast that can actually save you a lot of time. Also, this is not just an intrusion detection or prevention system. Security Onion is a complete Linux distribution along with a focus on intrusion detection, enterprise security monitoring, and log management as well.
This is written to operate on Ubuntu, Security Onion integrates elements from analysis tools and also front-end systems. These also include NetworkMiner, Snorby, Xplico, Sguil, ELSA, and Kibana as well. However, it is categorize as NIDS, Security Onion includes many HIDS functions as well.
Complete Linux distribution along with focus on log management, enterprise security monitoring, and also intrusion detection. Runs on Ubuntu integrates elements from many front-end analysis tools. That includes NetworkMiner, Snorby, Xplico, Sguil, ELSA, and Kibana also. It includes HIDS functions as well, a packet sniffer performs network analysis, including nice graphs and charts as well.
Sagan | intrusion detection software for windows
Sagan is actually a free-to-use HIDS and is one of the best alternatives to OSSEC. Well, a great thing about this IDS is that it is compatible with data collected by a NIDS such as Snort. Although it has many IDS-like features, Sagan is more of a log analysis system than an IDS actually.
The compatibility of Sagan is not actually limited to Snort; rather, it basically extends to all the tools. That can be integrated along with Snort also including Anaval, Squil, BASE, and Snorby. Plus, you can also install the tool on Linux, Unix, and also Mac-OS. Furthermore, you can also feed it with Windows event logs.
Last but not least, it can also implement IP bans through working with Firewalls. Whenever it detect suspicious activity from a particular source.
Conclusion
Alright, That was all Folks! I hope you guys like this “intrusion detection software for windows” article and also find it helpful to you. Give us your feedback on it. Also if you guys have further queries and issues related to this article. Then let us know in the comments section below. We will get back to you shortly.
Have a Great Day!
Also See: Best Sites for Amazon Background Check






