The exponential growth in mobile use has drastically changed the way people work and live. According to Statista, mobile internet traffic has observed a phenomenal rise from 48.8% to 64.3% globally. Thanks to constant innovations in mobile applications, mobile ecosystems are becoming sophisticated by the hour.
Since user experience is the crucial aspect that makes or breaks an application, it has made it rather challenging for businesses to continually upgrade their offerings and deliver an optimal user experience within tight deadlines.
No wonder mobile app testing has become a vital component of the mobile app development process to deliver robust applications.
However, many myths surround this concept. In this article, we will debunk the myths and explain why mobile security testing is the need of the hour. But first, let us understand what the term means.
Contents
- 1 What is mobile app security testing?
- 2 Why is mobile app security important?
- 3 Techniques to help make your app bug-free?
- 4 Debunking myths about mobile app security
- 4.1 #Myth 1: Testing is only needed for apps dealing with sensitive information.
- 4.2 #Myth 2: Testing comes after the app has been developed.
- 4.3 #Myth 3: Testing applications on emulators are adequate.
- 4.4 #Myth 4: Testing mobile apps is similar to testing web apps.
- 4.5 #Myth 5: One device each of Android and iOS is enough to test.
- 4.6 #Myth 6: Static source code testing suffices for mobile.
- 4.7 #Myth 7: Mobile apps are secure because Apple and Google test them.
- 4.8 Wrapping it up
What is mobile app security testing?
Short for MAST, it is the process of swiftly implementing server-side code, client-side code, and third-party analysis to identify and fix security vulnerabilities in mobile apps without the need for source code.
This form of testing is conducted to +confirm the app collects only the required information; thus, preventing unauthorized access and data modification while in use.
Why is mobile app security important?
According to Gartner, 90% of the companies today test their mobile apps for security vulnerabilities. Shockingly, cyber-attacks cost US enterprises an average of $1.2 million annually, while SMBs have to manage the damage of $117,000.
So, whether your Android or iPhone app solution falls into gaming, banking, eCommerce, or any other domain, you must ensure a regular security check to avoid hefty losses. Moreover, if you fail to test and update your app’s security measures post-release, your customers’ data could be at risk. The cost of a data breach for businesses has grown by 11% since 2017.
Hence, without an exact security protocol, you are at constant threat of data exposure and cyber-attacks that will result in the loss of your revenue and customer trust—both of which are hard to regain. Bottom line: make mobile app security testing a part of your design process from the very beginning.
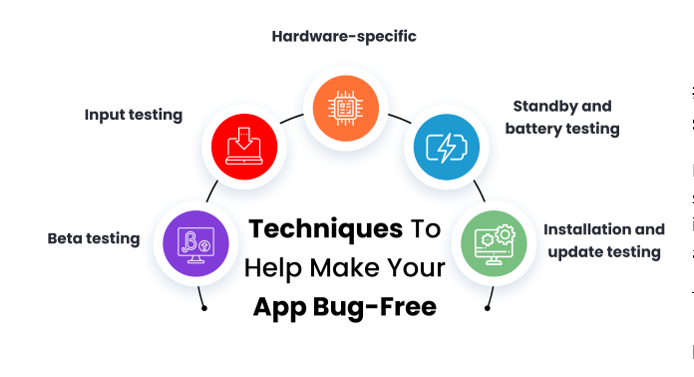
Techniques to help make your app bug-free?
Mobile app testers should conduct the following test to ensure the app is safe and secure:
- Beta testing
- Input testing
- Hardware-specific
- Standby and battery testing
- Installation and update testing
Debunking myths about mobile app security
#Myth 1: Testing is only needed for apps dealing with sensitive information.
It would be nice if testing is essential for mobile apps dealing with sensitive information, but it is not true. Hackers are not just interested in collecting customers’ profile picture, email address, and credit card details.
They are also interested in any Personally Identifiable Information [PII], such as a home address, mobile number, IP address, which can be used to trace an individual identity or a specific individual.
Such sensitive data is then sold at online black markets and spammers who then use it to make fraud calls for loan applications, purchase credit cards, do money transfers, and more. In short, information that may not seem private also needs to be protected on the mobile app to avoid any data leaks.
#Myth 2: Testing comes after the app has been developed.
Gone are those days when a mobile app would be tested in the final development phase. Today, development and testing go hand-in-hand. When done so, the QA team can quickly report bugs and errors to be fixed by the developers. Since even a 10% change in code gets tested beforehand, the entire development cycle shrinks without causing unnecessary increases in the company budget. Finding and fixing glitches in the app after it has been fully developed only delays its market launch and burns a hole in the pocket of businesses. Follow this simple in-depth guide on iPhone app development and conduct a thorough mobile app security test for superior results for your iOS apps.
#Myth 3: Testing applications on emulators are adequate.
Though the program might bear fruits in the early stage of development, it does not guarantee quality applications in the long run—in any way. As emulators do not contain any hardware [e.g., chipset and memory], they cannot perform real-time events such as battery drainage, screen visibility, or overheating in outdoor conditions.
Furthermore, testing on emulators would not give a clear picture of the mobile app performance on different platforms, such as Android and iOS. If you want to build an app that works well, conduct real device testing for accurate results. It will help the QA team to detect the errors faced by real-time users. One of the best and easiest ways to conduct mobile testing is on a cloud device.
#Myth 4: Testing mobile apps is similar to testing web apps.
No, that is entirely untrue! There is a misconception that mobile apps and web apps have the same testing tools and techniques. However, web app security testing bridges the web app code and APIs using SAST tools. That means the browser is isolated from the client machine where all code sits behind the firewall on the server, and the former handles the communication securely.
Mobile apps, on the other hand, have a full-device OS sitting underneath them. Since apps interact with other apps, that arrangement may be malicious. That is what makes mobile app security testing more complex. A constant eye needs to be kept at the data as it interacts with the device and when the data is transmitted across the network.
#Myth 5: One device each of Android and iOS is enough to test.
As Android and iOS platforms are highly diverse in terms of specifications such as memory, chipsets, OS versions, screen resolutions, testing the app only on select mobile devices from Google and Apple will not work. As app behavior differs in different OS versions, optimizing an app for an extensive device range is essential to ensure an optimal user experience. Therefore, the development team should cover maximum OS and platforms for comprehensive testing.
#Myth 6: Static source code testing suffices for mobile.
It is not true. Static application security testing [SAST] testing misses two large groups of the mobile attack surface, which are “data at rest “and data in motion” For instance; it does not address flag store issues such as a decrypted keychain, data caching, data in log files or SD card.
Neither does it assess vulnerabilities during data transition, such as session hijacking, fake TLS certificate, and improper TLS validation. Therefore, to conduct a proper test, you need to download the mobile app on the device called dynamic testing. A combination of static and dynamic testing can help you get an accurate view of how your app works.
#Myth 7: Mobile apps are secure because Apple and Google test them.
In reality, the two tech giants focus on enabling an ecosystem for mobile apps. They leverage tools and frameworks that help developers build secure and scalable mobile apps. They check if the app is compliant with their API guidelines and is free from any malware and static vulnerabilities. However, they do not check on data leakage, privacy issues, or third-party libraries that a mobile app uses. So, it is evident that the development team’s responsibility is to make their code secure.
Wrapping it up
If you have been taking mobile app security testing lightly, hopefully, this article will make you sit up and take notice. You cannot play with your customers’ data, nor can you hamper your brand reputation in the process.






